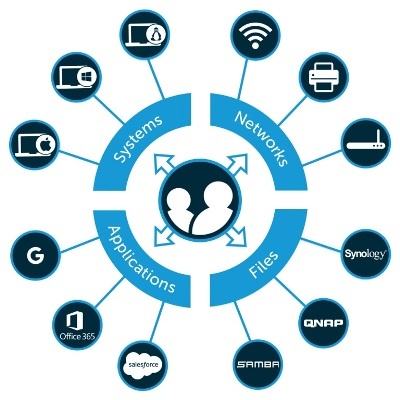
Identity Management
Identity management is the organizational process for identifying, authenticating and authorizing individuals or groups of people to have access to applications, systems or networks by associating user rights and restrictions with established identities. It refers to the IT security discipline, framework, and solutions for managing digital identities.
ID management determines whether a user has access to systems, but also sets the level of access and permissions a user has on a particular system. Identity management includes authenticating users and determining whether they’re allowed access to particular systems.
The overarching goal
for IAM is to ensure that any given identity has access to the right resources
(applications, databases, networks, etc.) and within the correct context.
The main goal of identity management is to ensure that only authenticated users
are granted access to the specific applications, systems or IT environments for
which they are authorized.
Identity management is an IT gatekeeping function in which users are provided or denied access to business data based on their organizational roles and individual credentials.
What:
Identity management is the discipline of managing access to enterprise
resources to keep systems and data secure.
About:
Identity management primarily supports business security and compliance by only
allowing explicitly credentialed users to access sensitive information. User
rights are controlled programmatically, providing a cost-efficient solution to
data security and privacy.
How:
The core of identity management is the creation and enforcement of policies
that determine which users have access to which resources, devices, and assets
in the network. By preventing users from accessing unauthorized resources, the
company increases security and productivity, and limits risk
from regulatory non-compliance.
Why:
Identity management solutions outfit IT with the means to establish identity of
all users in the enterprise and control their access to any federated device or
data. These products make it easy to apply business policies to users, taking
into account dependent conditions such as wireless or wired access and secured
connectivity versus sensitivity of information. Thus the organization is
prevented from putting data at risk, while also supporting stakeholders in moving
critical business processes forward. Identity management enforces
device-specific authentication to improve the organization’s mobile security
posture.